Do you know what have your users done?
What is User Behaviour Analysis
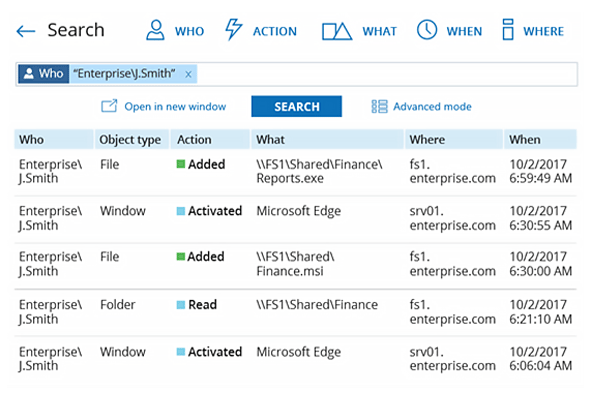
- User Behavior Analytics or UBA focuses on what the user is doing: apps launched, network activity, and, most critically files accessed (when the file or email was touched, who touched it, what was done with it and how frequently).
- User behavior analysis is one part of a multilayered, integrated IT and information security strategy to prevent attacks and investigate threats. It can be an incredibly powerful tool to detect compromise early, mitigate risk, and stop an attacker from exfiltrating an organization’s data.
Top 9 abnormal user behavior
Unknown new AD admin user
- Keep an eye on any new members in AD admin group
Unauthorized Access
- Repeated access for the unauthorized folder / accounts
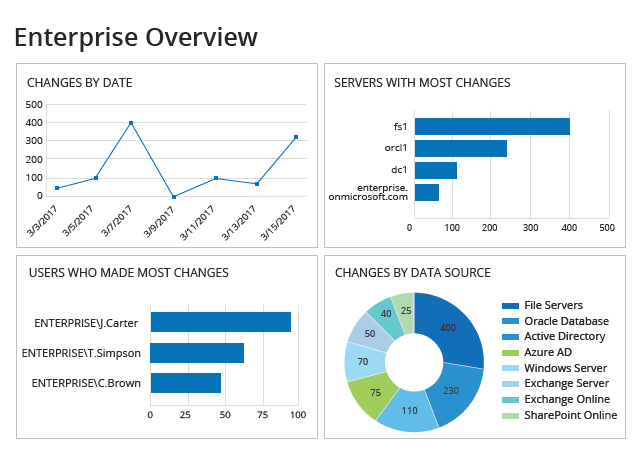
Massive changes in servers
- Massive changes: deletion, modification, read in the file servers
Suspicious ransomware detection
- creation for many encrypted files
Temp. user created and removed
- unauthorised creation and removal of account
Huge amounts of user file and email activity
- Investigation to massive user activities
Multiple login locations within 10 minutes
- multiple logins from different locations within 10 minutes
User Activity Surges
- Action surges abnormally compared with before
Monitoring for third party vendor activity
- Video recording for access from third party vendors
SIEM vs UBA (User Behavior Analysis)
User Behavior Analysis
UBA focuses on what the user is doing: apps launched, network activity, and, most critically files accessed (when the file or email was touched, who touched it, what was done with it and how frequently).
The main focus of UBA will be on abnormal user activities. for example, if one single user changed 100 files during the last 15 minutes. It is an abnormal event which should be investigated.
Security and Incident Event Management ( SIEM )
SIEM has focused on analyzing events captured in firewalls, OS, and other system logs in order to spot interesting correlations, usually through pre-defined rules.
For example, several login failure events in one log might be matched to increased traffic exiting the network recorded in yet another log. SIEM might decide this is a sign of hackers entering the system and removing data.
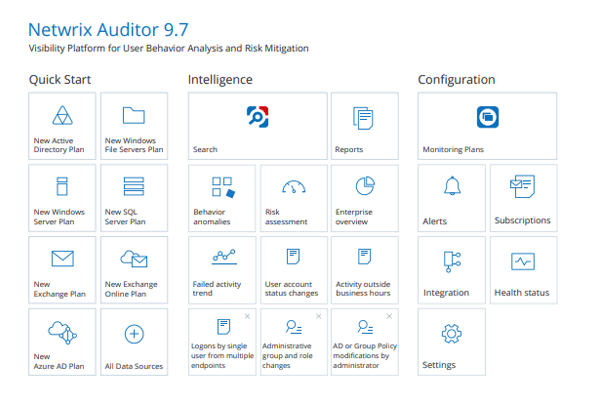
Integrated solution for User Behavior Analysis
Abnormal user behavior
detected from Netwrix Auditor


William deleted 100 files within last 10 minutes


A sales manager, leaving company next month, is now copying 30 files from confidential folders / SQL in last 15 minutes


Ken Wong became admin user last night and rolled back after one hour last night

Massive file extension changed to encryption format from last 15 minutes


Permission changes for confidential folders

Repeated failed logon for the same user on critical applications and folders
Netwrix Auditor detection steps
What’s NEXT?
TIL provides remote demo, technical material, ballpark figure and solution advisory