Data Security Solutions
DATA SECURITY NEWS in Hong Kong 2019
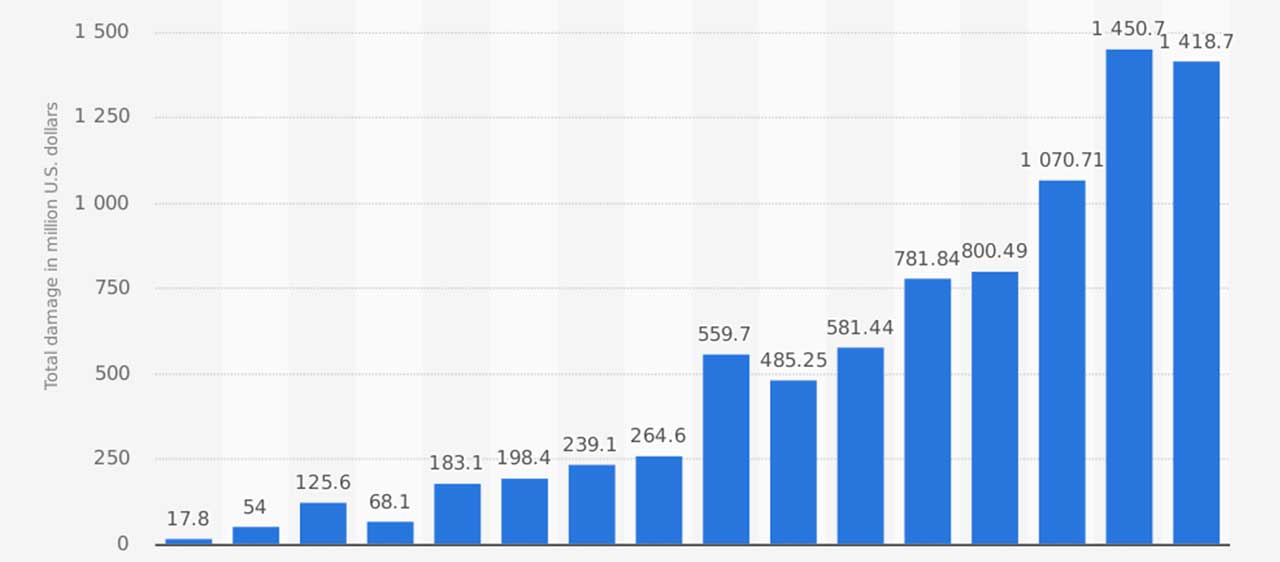
Financial losses increase 565% since 2012 to 2018 from cybersecurity
565% increase of financial loss from cybersecurity ( reaching $ 2.26 Billion)
view details
Cathay Pacific data leak
Cathay Pacific revealed that the data of 9.4 million passengers had been illegally accessed.
view details

Credit reporting agency TransUnion forced to suspend online services
The Hong Kong arm of American consumer credit reporting agency TransUnion was forced to suspend its online services after a local newspaper was easily able to access the personal data of Hong Kong Chief Executive and finance minister.
view details

Do you want to the next story in the press?
TOP data security breach incidents

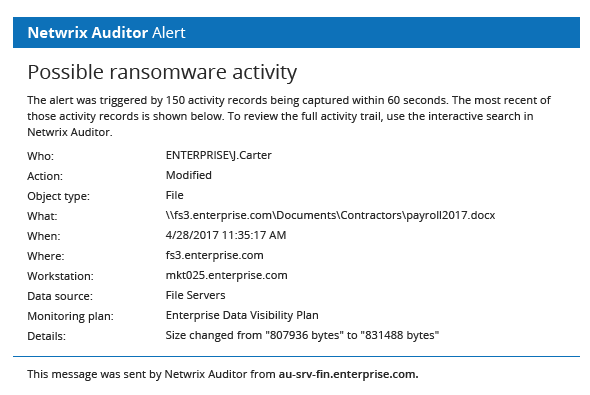
Ransomware
- With ransomware attacks growing in both number in Hong Kong, organizations need a solid, multi-layer defense strategy that helps them detect any suspicious ransomware and react quickly, so they can limit the impact on data and operations.

Confidential data leakage
- Data leakage is the unauthorized transmission of data from within an organization to an external destination or recipient. The term can be used to describe data that is transferred electronically or physically. Data leakage threats usually occur via the web and email, but can also occur via mobile data storage devices such as optical media, USB keys, and laptops.

Third party vendor unauthorized access
- Hong Kong enterprises usually get support from third-party vendors which can access critical servers and data. This is important to keep all actions taken from data security breach.
What SOLUTIONS can help?
Netwrix Auditor Security Suite
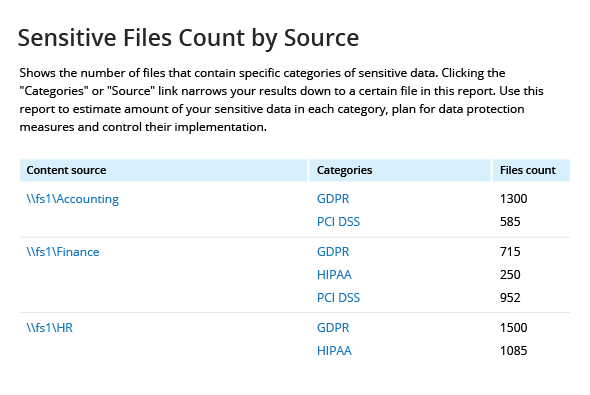
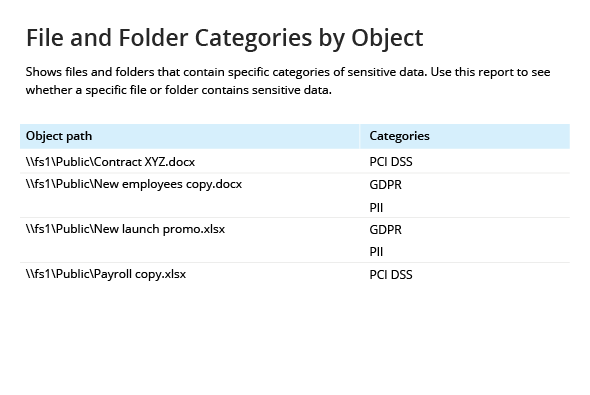
Data Classification
- Identify file shares and specific folders that contain sensitive files so you can prioritize the data security of these assets. Ensure that only authorized personnel can view, edit, share or delete these files; carefully monitor activity that might jeopardize the data security; and detect any sensitive data surfaces outside of a secure location.
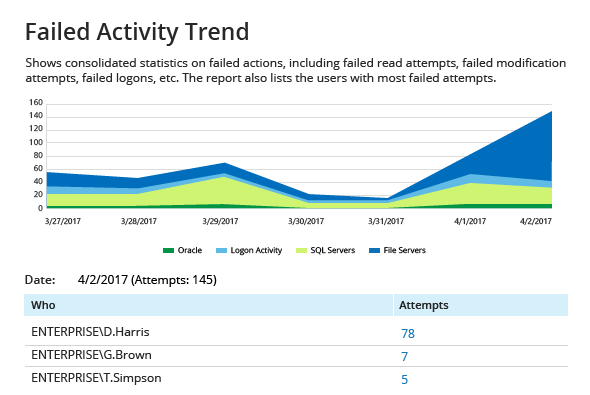
Data Security Event Discovery
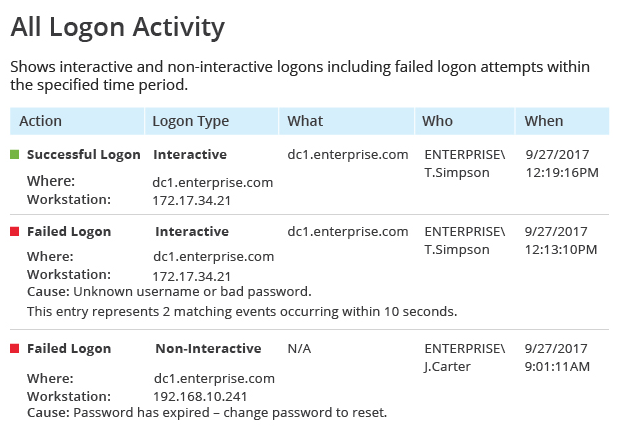
Permission review
To ensure only the right user have access to specific data.
Validating the effective permissions and group memberships for a specific user or a group across AD and file shares. Netwrix delivers a full picture of your current effective permissions and enabling you to spot users with unnecessary access.
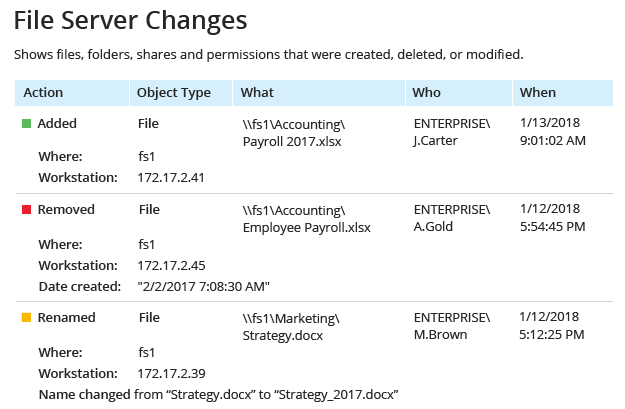
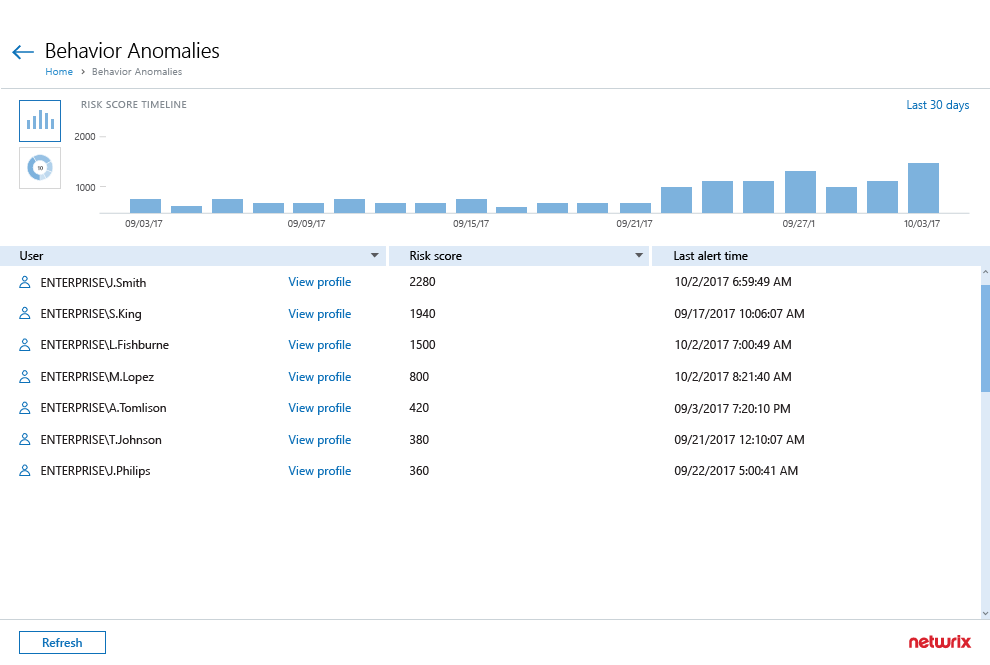
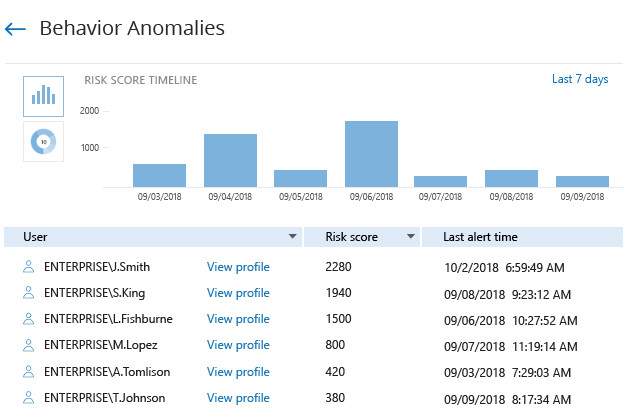
Data Security Investigation
- Quickly identify subtle signs of possible threats, such as unusual logons that might indicate user identity theft or a disgruntled privileged user trying to hide his or her activity behind temporary accounts. With the user behavior and blind spot analysis reports, no malicious activity can slip under your radar.
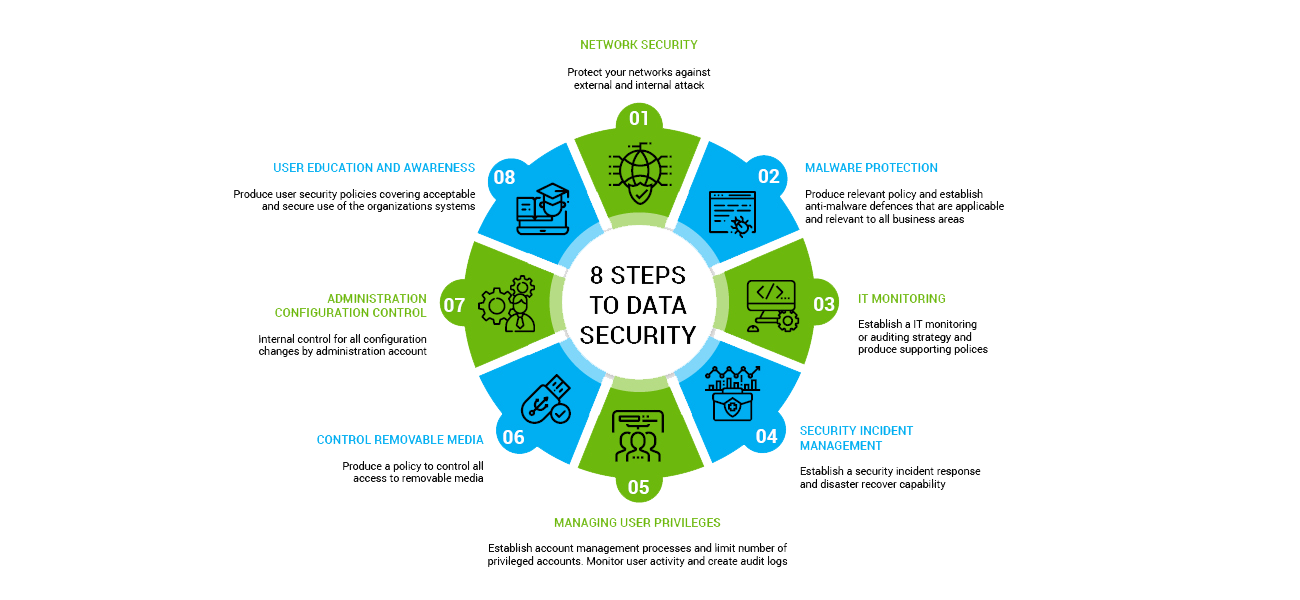
8 Steps to Data Security
Netwrix is fulfilling your 8 ultimate data security steps.

What’s NEXT?
TIL provides remote demo, technical material, ballpark figure and solution advisory